Practice analyzing malicious traffic using Brim.
Link: https://tryhackme.com/room/mastermindsxlq
“Note: Before attempting this room, it is highly recommended that you complete the Zeek and Brim rooms. Those mentioned rooms cover basic security concepts and processing Zeek log files, which will help you navigate this room effectively.”
“Three machines in the Finance department at Pfeffer PLC were compromised. We suspect the initial source of the compromise happened through a phishing attempt and by an infected USB drive. The Incident Response team managed to pull the network traffic logs from the endpoints. Use Brim to investigate the network traffic for any indicators of an attack and determine who stands behind the attacks.”
Task 2: [Infection 1]
Provide the victim’s IP address.
Ans: 192.168.75.249
We will use the built-in queries to identify the victim IP. “192.168.75.249” is the correct IP as we can see from the image, it is the only internal IP address that is communicating to other external IP.
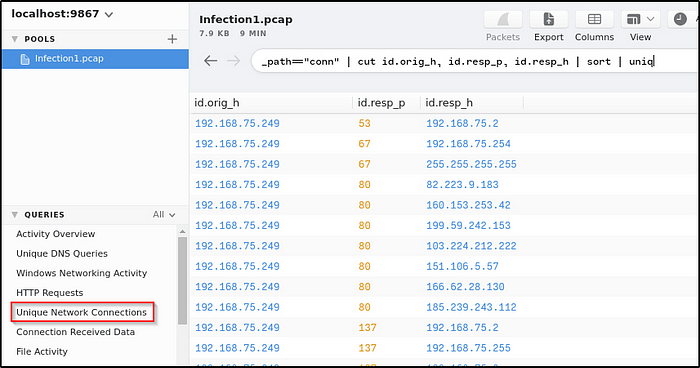
Another way to identify the IP address is by analyzing the total bytes transferred between endpoints.
_path=="conn" | put total_bytes := orig_bytes + resp_bytes | sort -r total_bytes | cut uid, id, orig_bytes, resp_bytes, total_bytes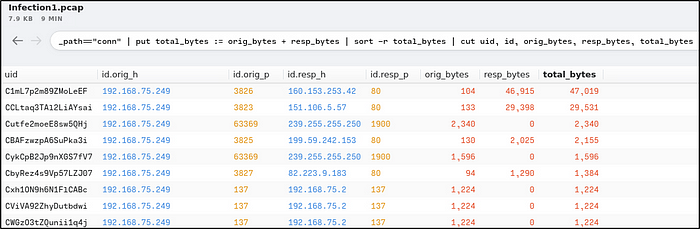
We can say, based from the results that “192.168.75.249” is the victim’s IP address because of its suspicious total number of bytes, and it is a private IP address.
The victim attempted to make HTTP connections to two suspicious domains with the status ‘404 Not Found’. Provide the hosts/domains requested.
Ans: cambiasuhistoria.growlab.es,www.letscompareonline.com
-path=="http" | status_code==404 | cut host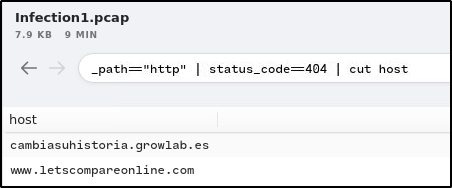
The victim made a successful HTTP connection to one of the domains and received the response_body_len of 1,309 (uncompressed content size of the data transferred from the server). Provide the domain and the destination IP address.
Ans: ww25.gocphongthe.com,199.59.242.153
_path=="http" | cut id.resp_h, host, status_code, response_body_len| 200 | 1309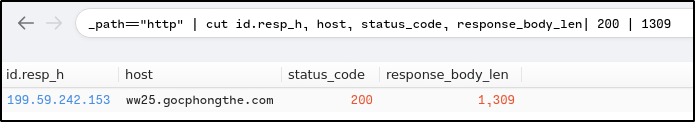
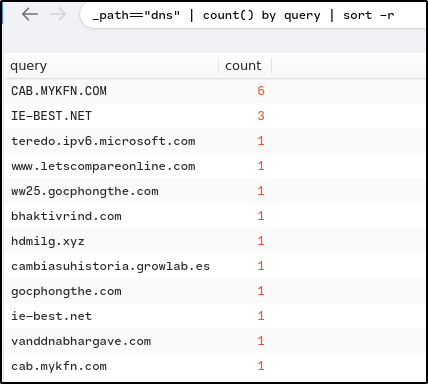
How many unique DNS requests were made to cab[.]myfkn[.]com domain (including the capitalized domain)?
Ans: 7
Provide the URI of the domain bhaktivrind[.]com that the victim reached out over HTTP.
Ans: /cgi-bin/JBbb8/
_path=="http" | cut host, uri | bhaktivrind.com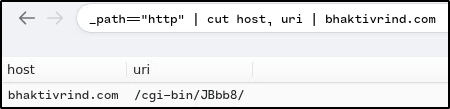
Provide the IP address of the malicious server and the executable that the victim downloaded from the server.
Ans: 185.239.243.112,catzx.exe
_path=="http" | cut id.orig_h, id.resp_h, id.resp_p, method,host, uri | uniq -c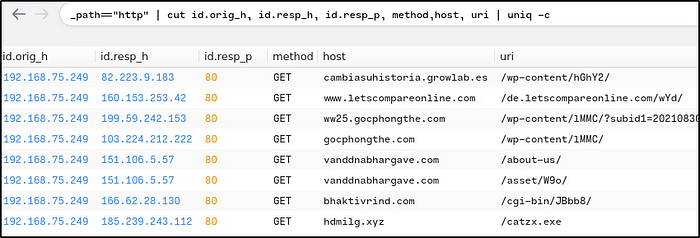
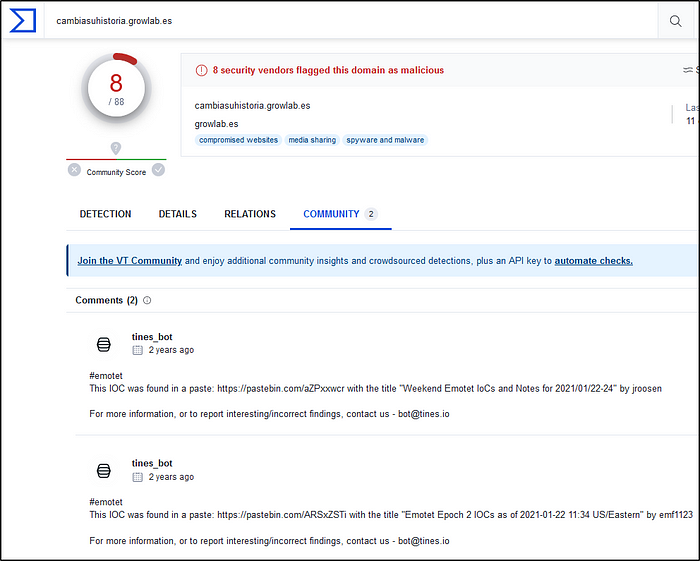
Based on the information gathered from the second question, provide the name of the malware using VirusTotal.
Ans: Emotet
Task 3 [Infection 2]
Provide the IP address of the victim machine.
Ans: 192.168.75.146
We are gonna use the same logic. Another thing to remember is that, the IP address is within the same subnet.
_path=="conn" | put total_bytes := orig_bytes + resp_bytes | sort -r total_bytes | cut uid, id, orig_bytes, resp_bytes, total_bytes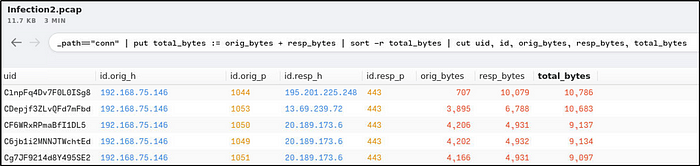
Another way to look for it, is using the built-in queries. The result clearly shows that there are numerous suspicious connections established to a single IP address, 192.168.75.1 is not included as IP addresses ending in “1” are gateways.
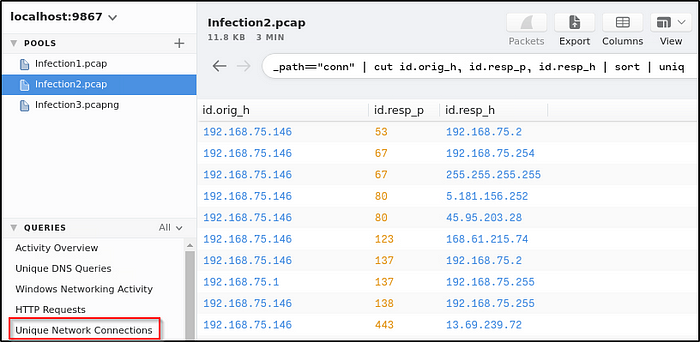
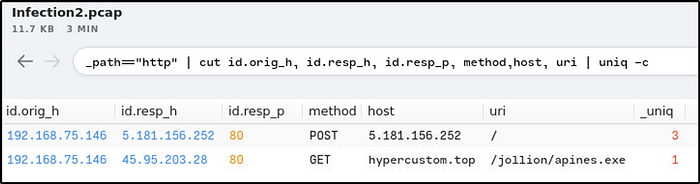
Provide the IP address the victim made the POST connections to.
Ans: 5.181.156.252
method=="POST" |192.168.75.146 | cut id.resp_h | sort -r | uniq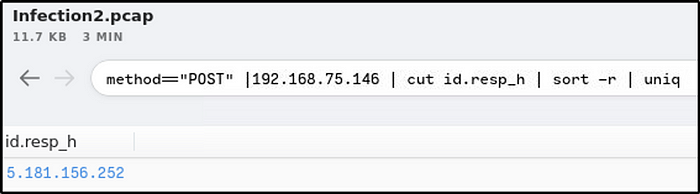
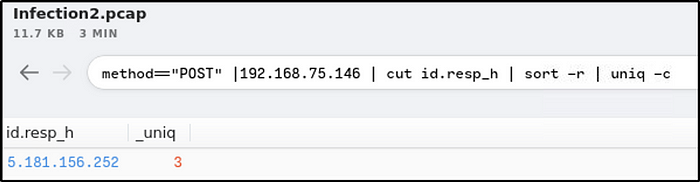
How many POST connections were made to the IP address in the previous question?
Ans: 3method==”POST” |192.168.75.146 | cut id.resp_h | sort -r | uniq -c
Provide the domain where the binary was downloaded from.
Ans: hypercustom.top
With this filter, we can also answer the two next questions.
_path=="http" | cut id.resp_h,host, uri, mime_type | uniq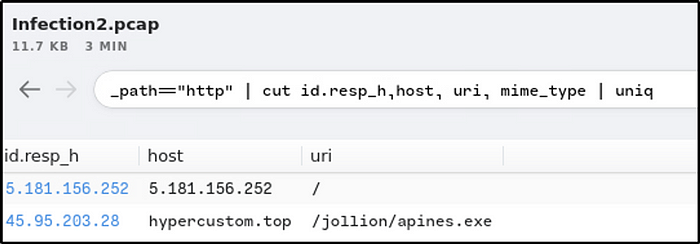
Provide the name of the binary including the full URI.
Ans: /jollion/apines.exe
Provide the IP address of the domain that hosts the binary.
Ans: 45.95.203.28
There were 2 Suricata “A Network Trojan was detected” alerts. What were the source and destination IP addresses?
Ans: 192.168.75.146,45.95.203.28
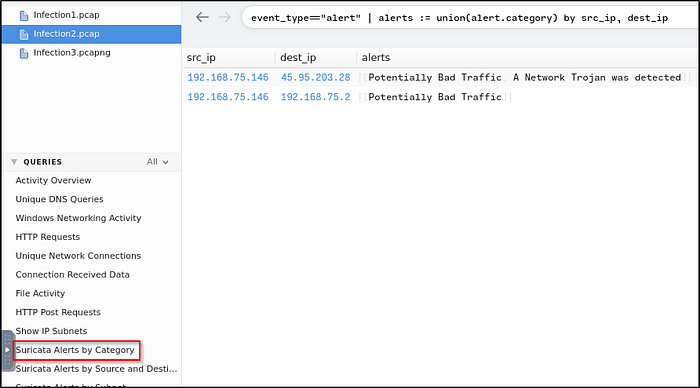
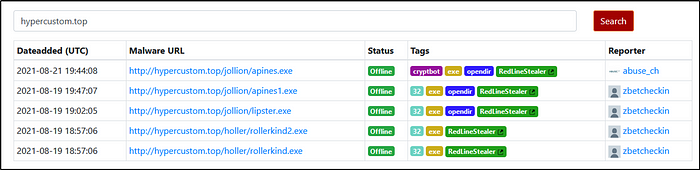
Taking a look at .top domain in HTTP requests, provide the name of the stealer (Trojan that gathers information from a system) involved in this packet capture using URLhaus Database.
Ans: Redline Stealer
Task 4 [Infection 3]
Provide the IP address of the victim machine.
Ans: 192.168.75.232
Same concept from the previous tasks, or I should say when analyzing network traffic.
_path=="conn" | put total_bytes := orig_bytes + resp_bytes | sort -r total_bytes | cut uid, id, orig_bytes, resp_bytes, total_bytes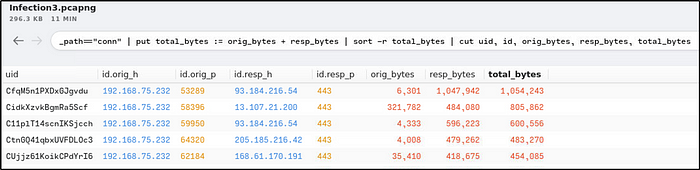
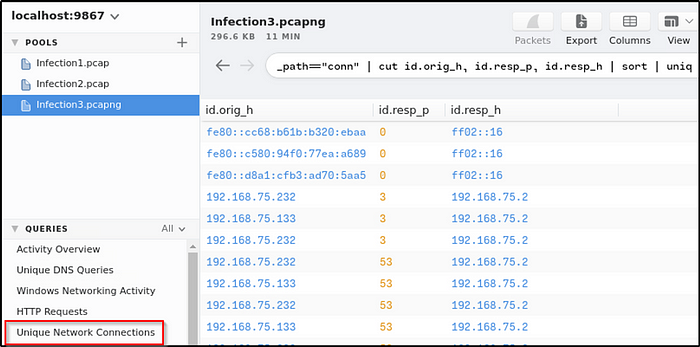
Provide three C2 domains from which the binaries were downloaded (starting from the earliest to the latest in the timestamp)
Ans: efhoahegue.ru,afhoahegue.ru,xfhoahegue.ru
_path=="http" | cut ts, id.orig_h, id.resp_h, id.resp_p, method, host, uri | uniq -c | sort ts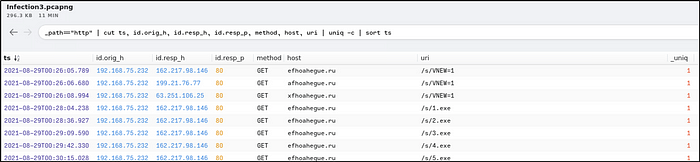
Provide the IP addresses for all three domains in the previous question.
Ans: 162.217.98.146,199.21.76.77,63.251.106.25
We get the answer from the previous question, as shown in the filter result.
How many unique DNS queries were made to the domain associated from the first IP address from the previous answer?
Ans: 2
_path=="dns" | count() by query | sort -r| efhoahegue.ru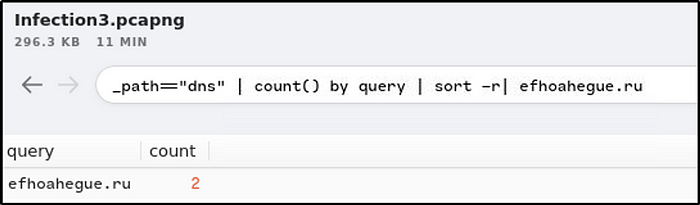
How many binaries were downloaded from the above domain in total?
Ans: 5
_path=="http" | efhoahegue.ru| cut uri, mime_type | uniq -c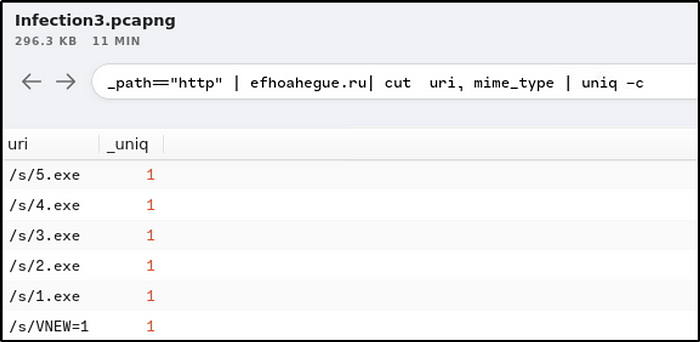
Provided the user-agent listed to download the binaries.
Ans: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:25.0) Gecko/20100101 Firefox/25.0
_path=="http" | efhoahegue.ru| cut uri, user_agent| uniq -c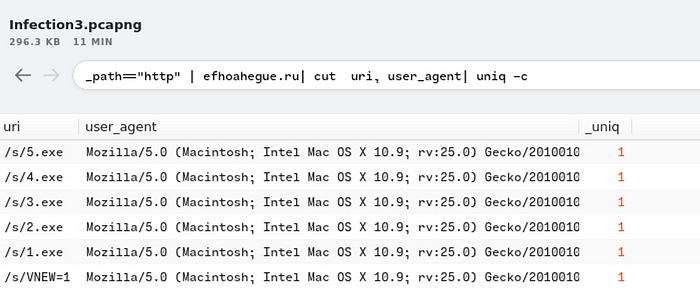
Provide the amount of DNS connections made in total for this packet capture.
Ans: 986
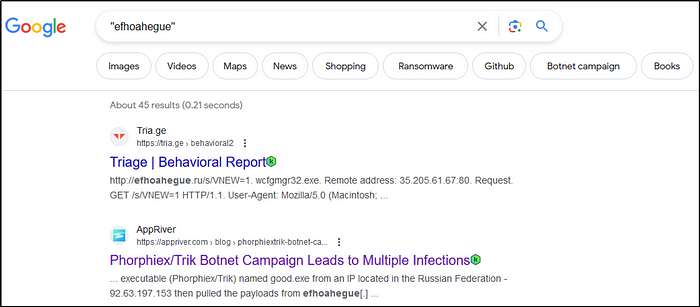
_path=="dns" | count() by query | sort -r count |sum(count)With some OSINT skills, provide the name of the worm using the first domain you have managed to collect from Question 2. (Please use quotation marks for Google searches, don’t use .ru in your search, and DO NOT interact with the domain directly).
Ans: Phorphiex
Thanks for reading! Happy learning 🙂


Leave a comment