In this post, I’ll explore Splunk with TryHackMe, a leading SIEM tool, to gain hands-on experience with its key capabilities. This room provides an overview of Splunk’s core components like forwarders, indexers, and search heads and how they work together for log collection and analysis. It also covers fundamental Splunk concepts like ingesting sample VPN logs, normalizing data into events, and searching using Splunk Processing Language (SPL).
Room link: Splunk: Basics
Task 1 : Introduction
Splunk is one of the leading SIEM solutions in the market that provides the ability to collect, analyze and correlate the network and machine logs in real-time. In this room, we will explore the basics of Splunk and its functionalities and how it provides better visibility of network activities and help in speeding up the detection.
Learning Objective and Pre-requisites
If you are new to SIEM, please complete the Introduction to SIEM. This room covers the following learning objectives:
- Splunk overview
- Splunk components and how they work
- Different ways to ingest logs
- Normalization of logs
Task 2: Connect with the Lab
Room MachineBefore moving forward, deploy the machine. When you deploy the machine, it will be assigned an IP. Access this room in a web browser on the AttackBox, or via the VPN at http://MACHINE_IP. The machine will take up to 3-5 minutes to start.
Task 3: Splunk Components
Splunk has three main components, namely Forwarder, Indexer, and Search Head. These components are explained below:

Splunk Forwarder
Splunk Forwarder is a lightweight agent installed on the endpoint intended to be monitored, and its main task is to collect the data and send it to the Splunk instance. It does not affect the endpoint’s performance as it takes very few resources to process. Some of the key data sources are:
- Web server generating web traffic.
- Windows machine generating Windows Event Logs, PowerShell, and Sysmon data.
- Linux host generating host-centric logs.
- Database generating DB connection requests, responses, and errors.

Splunk Indexer
Splunk Indexer plays the main role in processing the data it receives from forwarders. It takes the data, normalizes it into field-value pairs, determines the datatype of the data, and stores them as events. Processed data is easy to search and analyze.

Search Head
Splunk Search Head is the place within the Search & Reporting App where users can search the indexed logs as shown below. When the user searches for a term or uses a Search language known as Splunk Search Processing Language, the request is sent to the indexer and the relevant events are returned in the form of field-value pairs.

Search Head also provides the ability to transform the results into presentable tables, visualizations like pie-chart, bar-chart and column-chart, as shown below:

Answer the questions below
Which component is used to collect and send data over the Splunk instance?
Answer: Forwarder
Task 4: Navigating Splunk
Splunk Bar
When you access Splunk, you will see the default home screen identical to the screenshot below.

Let’s look at each section, or panel, that makes up the home screen. The top panel is the Splunk Bar (below image).

In the Splunk Bar, you can see system-level messages (Messages), configure the Splunk instance (Settings), review the progress of jobs (Activity), miscellaneous information such as tutorials (Help), and a search feature (Find).
The ability to switch between installed Splunk apps instead of using the Apps panel can be achieved from the Splunk Bar, like in the image below.

Apps Panel
Next is the Apps Panel. In this panel, you can see the apps installed for the Splunk instance.
The default app for every Splunk installation is Search & Reporting.

Explore Splunk
The next section is Explore Splunk. This panel contains quick links to add data to the Splunk instance, add new Splunk apps, and access the Splunk documentation.

Splunk Dashboard
The last section is the Home Dashboard. By default, no dashboards are displayed. You can choose from a range of dashboards readily available within your Splunk instance. You can select a dashboard from the dropdown menu or by visiting the dashboards listing page.

You can also create dashboards and add them to the Home Dashboard. The dashboards you create can be viewed isolated from the other dashboards by clicking on the Yours tab.
Please review the Splunk documentation on Navigating Splunk here.
Answer the questions below
In the Add Data tab, which option is used to collect data from files and ports?
Answer: Monitor

Task 5: Adding Data
Splunk can ingest any data. As per the Splunk documentation, when data is added to Splunk, the data is processed and transformed into a series of individual events.
The data sources can be event logs, website logs, firewall logs, etc.
Data sources are grouped into categories. Below is a chart listing from the Splunk documentation detailing each data source category.

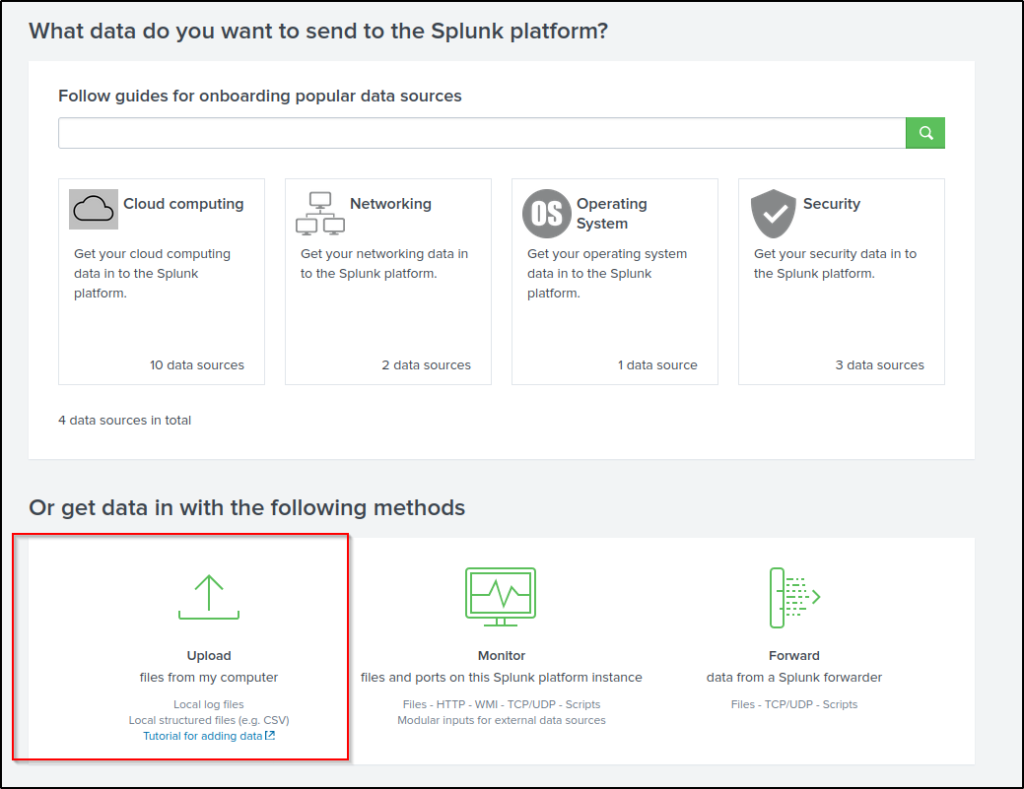
In this room, we’re going to focus on VPN logs. When we click on the Add Data link (from the Splunk home screen), we’re presented with the following screen.

We will use the Upload Option to upload the data from our local machine. Download the attached log file and upload it on Splunk.
As shown above, it has a total of 5 steps to successfully upload the data.
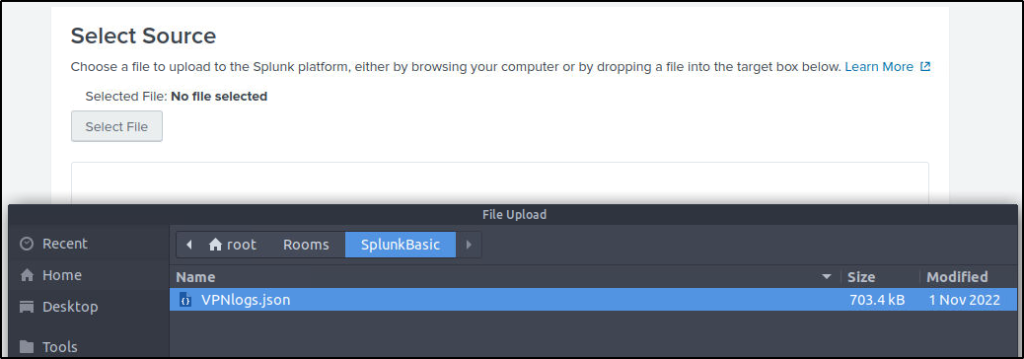
- Select Source -> Where we select the Log source.
- Select Source Type -> Select what type of logs are being ingested.
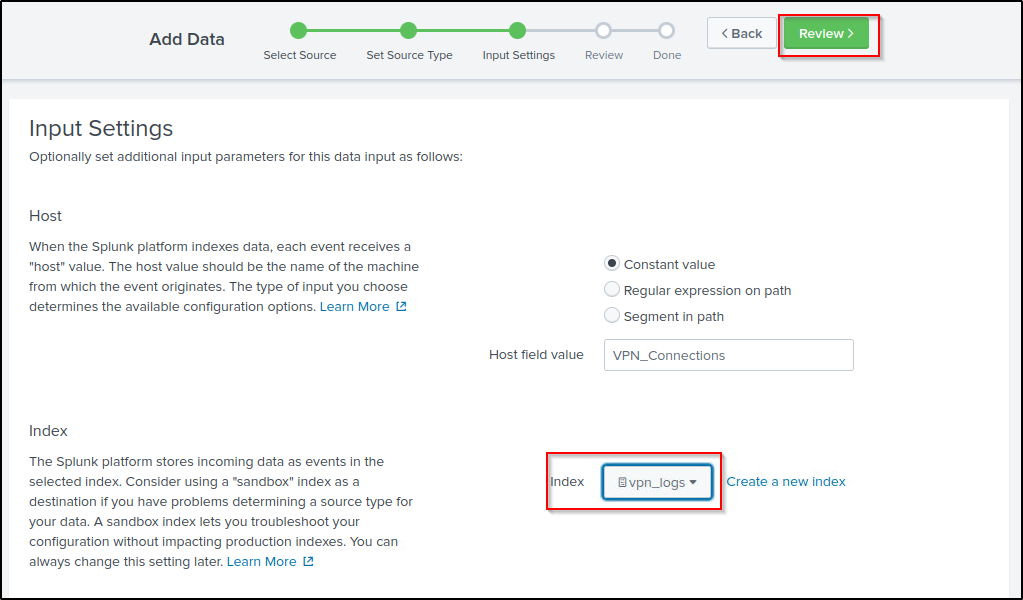
- Input Settings ->Select the index where these logs will be dumped and hostName to be associated with the logs.
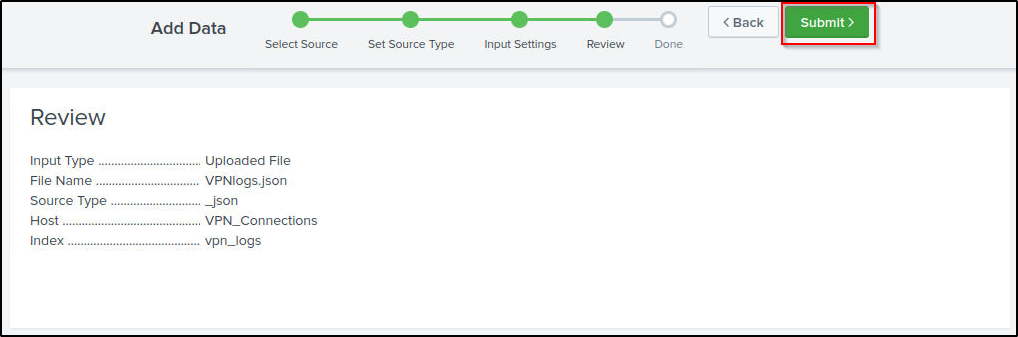
- Review -> Review all the gif
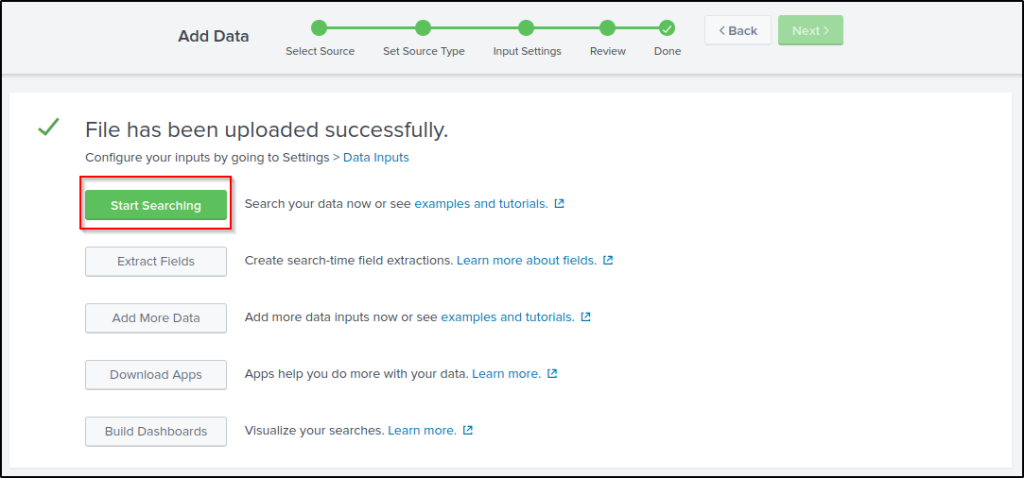
- Done -> Final step, where the data is uploaded successfully and ready to be analyzed.

As you can see, there are A LOT more logs we can add to the Splunk instance, and Splunk supports various source types.
Download the attached log file “VPN_logs” and upload this file into the Splunk instance with the right source type.
Note: In case you are using the AttackBox, the file is available in the /root/Rooms/SplunkBasic/ directory.
Navigate to the Explore Splunk section and click on the “Add Data”.
Select “Upload”.
Navigate to the location of the file.
Click “Next” after the file has been uploaded.

Choose “_json” as the source type.
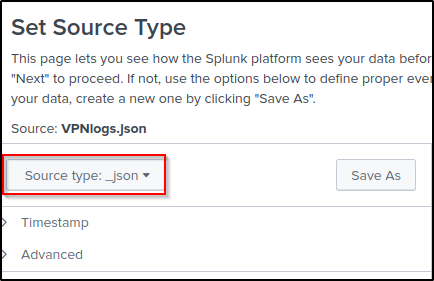
Edit the Host field value.
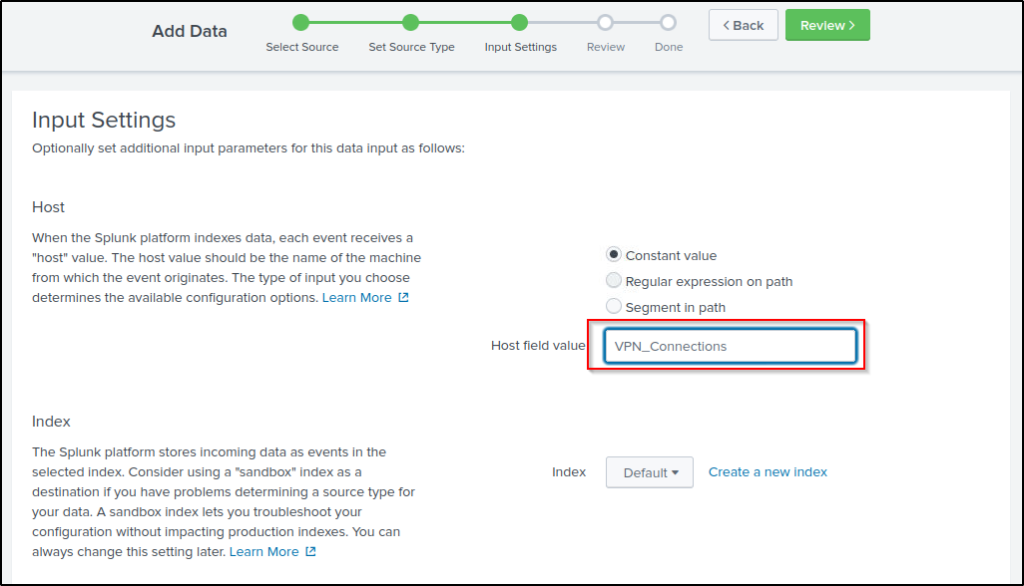
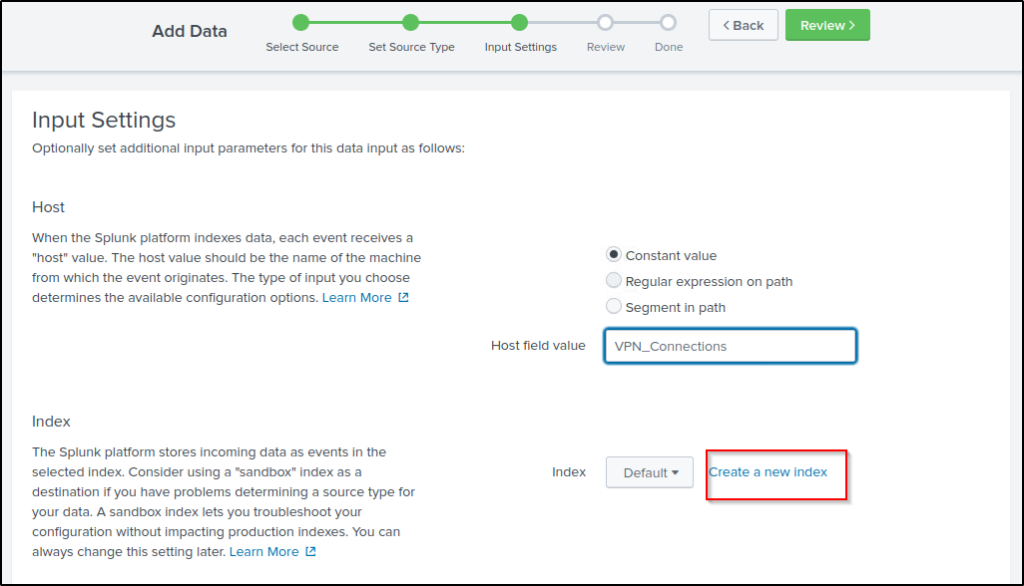
Create a new index.
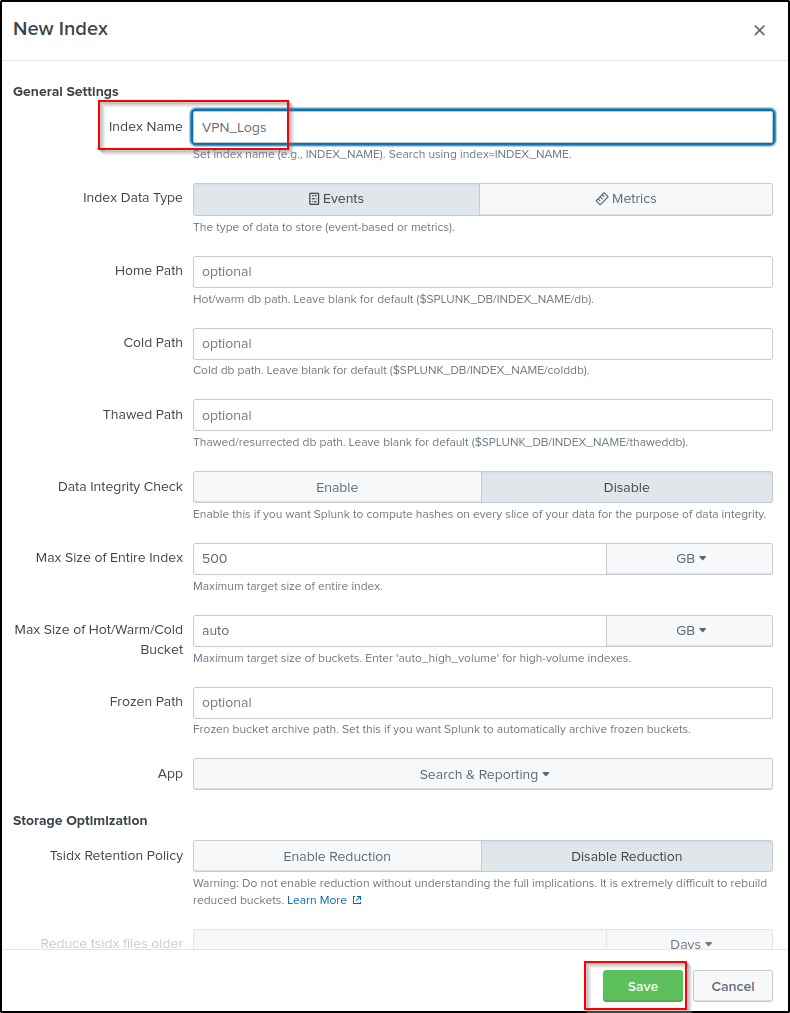
Create a name for the index and save.
Choose the newly created index then click on “Review”
Review to ensure settings are correct then submit.
Click on “Start Searching” to begin searching for events within the data.
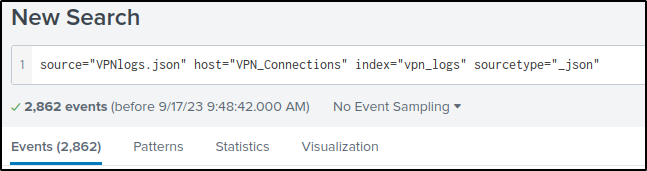
The image below is the default window displayed with a total of 2,862 events.
Answer the questions below
Upload the data attached to this taskand create an index “VPN_Logs”. How many events are present in the log file?
Answer: 2862
See the last image from above.
How many log events by the user Maleena are captured?
Answer: 60
There is a field named “UserName” in the left panel. I will filter events using that field to display events related to the user “Maleena” only.
source="VPNlogs.json" host="VPN_Connections" index="vpn_logs" sourcetype="_json" UserName=Maleena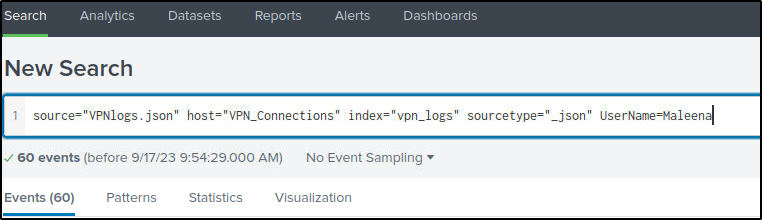
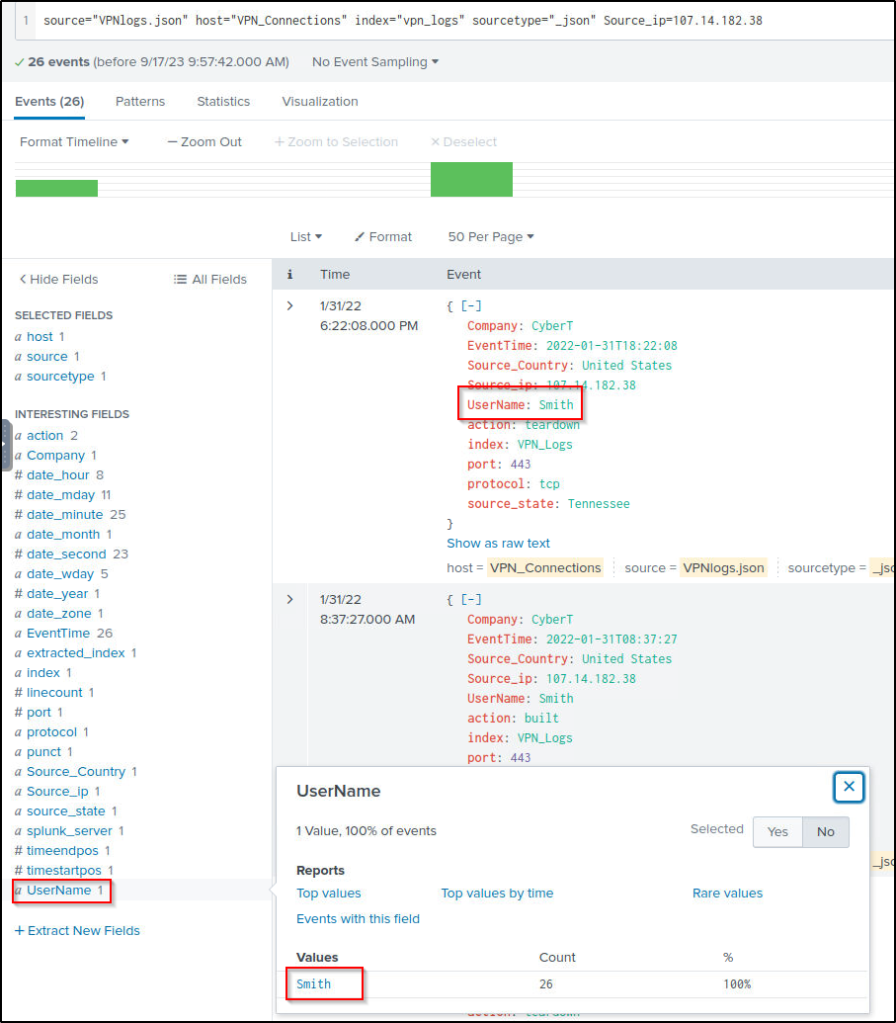
What is the name associated with IP 107.14.182.38?
Answer: Smith
The following query will filter only events coming from IP adress 107.14.182.38.
source="VPNlogs.json" host="VPN_Connections" index="vpn_logs" sourcetype="_json" Source_ip=107.14.182.38The value of the “UserName” is found on the left panel or in the event itself when expanded.
What is the number of events that originated from all countries except France?
Answer: 2814
I used the logical operator “NOT” to not include events whose source country is from “France”.
source="VPNlogs.json" host="VPN_Connections" index="vpn_logs" sourcetype="_json" NOT Source_Country="France"
How many VPN Events were observed by the IP 107.3.206.58?
Answer: 14
The query will filter events only from IP address 107.3.206.58.
source="VPNlogs.json" host="VPN_Connections" index="vpn_logs" sourcetype="_json" Source_ip=107.3.206.58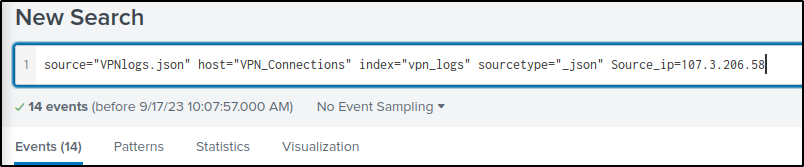
Task 6: Conclusion
In this room, we explored Splunk, its components, and how it works. Please check the following Splunk walkthrough and challenge rooms to understand how Splunk is effectively used in investigating the incidents.
In this post, I explored the foundational concepts and capabilities of the Splunk SIEM. By ingesting and searching sample VPN logs, I gained experience with Splunk’s log management and analysis functionality. Splunk’s forwarders, indexers, and search heads work together to collect, process, and analyze security data. Mastering Splunk takes time, but this post provided core knowledge and skills to start using Splunk for monitoring, threat hunting, and incident response.
Thank you for reading. Until next time 🙂


Leave a comment