Investigating the Compromised Endpoint
Scenario: One of the employees at Lockman Group gave an IT department the call; the user is frustrated and mentioned that all of his files are renamed to a weird file extension that he has never seen before. After looking at the user’s workstation, the IT guy already knew what was going on and transferred the case to the Incident Response team for further investigation.
You are the incident responder. Let’s see if you can solve this challenge using the infamous Redline tool. Happy Hunting, my friend!
To start your investigation, open the Mandiant Analysis file in the Analysis File folder on the Desktop.
Note: Loading the Mandiant Analysis file may take 2-3 minutes.
Deploy the machine attached to this task; it will be visible in the split-screen view once it is ready.
If you don’t see a virtual machine load then click the Show Split View button.

If you wish to access the virtual machine via Remmina, use the credentials below.
Machine IP: MACHINE_IP
User: administrator
Password: letmein123!

Accept the Certificate when prompted, and you should be logged into the remote system now.
Note: The virtual machine may take up to 3 minutes to load.
Answer the questions below
Open the the “Analysis File” folder on the Desktop.
Double click on “AnalysisSession1” file and Redline will import the data.

What is the compromised employee’s full name?
Answer: John Coleman
Under “System Information”, the employee’s name is found in the “User Information” section.
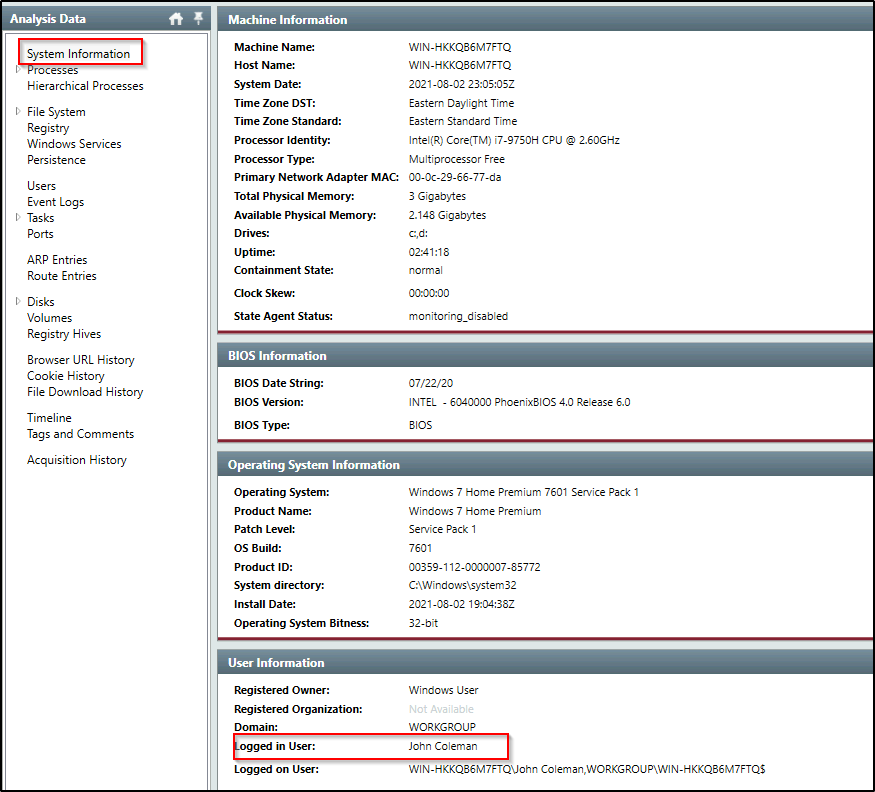
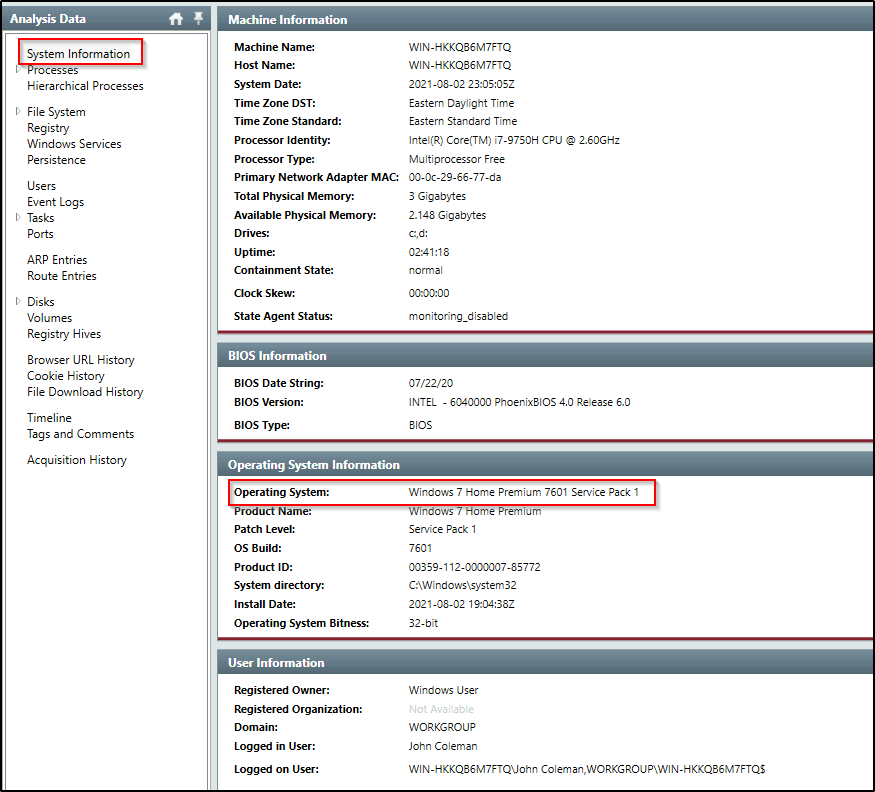
What is the operating system of the compromised host?
Answer: Windows 7 Home Premium 7601 Service Pack 1
Look at the “Operating System Information”
What is the name of the malicious executable that the user opened?
Answer: WinRAR2021.exe
Scroll down to the “File Download History” which contains the name of the executable.
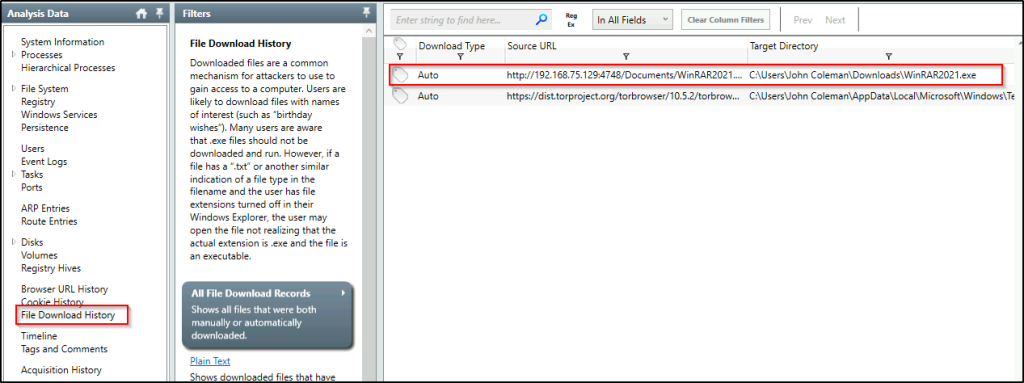
What is the full URL that the user visited to download the malicious binary? (include the binary as well)
Answer: http://192.168.75.129:4748/Documents/WinRAR2021.exe
See above image.
What is the MD5 hash of the binary?
Answer: 890a58f200dfff23165df9e1b088e58f
Click on “File System” and filter the results pointing to the user’s “Download” directory.
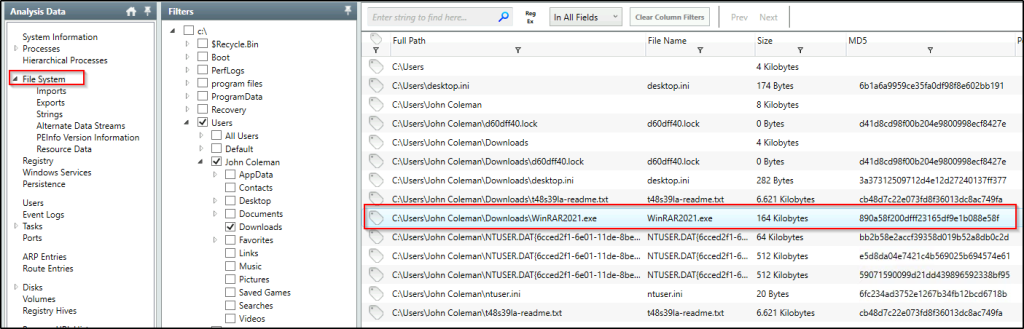
What is the size of the binary in kilobytes?
Answer: 164
See above image.
What is the extension to which the user’s files got renamed?
Answer: .t48s39la
Change the filter to point on the user’s Desktop directory. We can see files where their extension were changed.
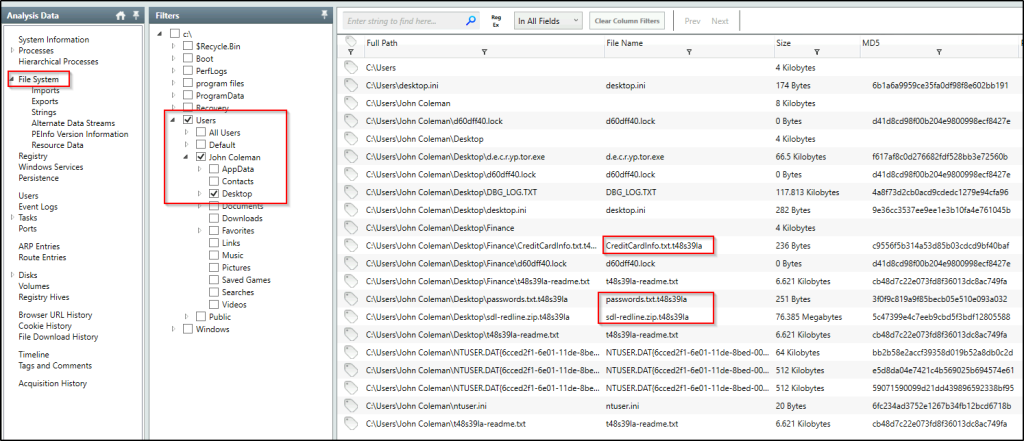
What is the number of files that got renamed and changed to that extension?
Answer: 48
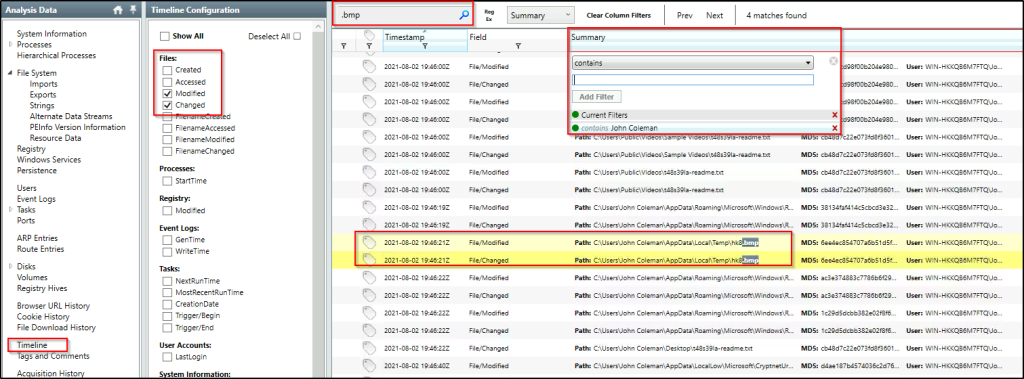
From the above filter, we were able to identify the extension. Go to “Timeline” and filter the files with “Modified” and “Changed” fields. In the search bar, type in the file extension identified and we see the number of files that match the extension.

What is the full path to the wallpaper that got changed by an attacker, including the image name?
Answer: C:\Users\John Coleman\AppData\Local\Temp\hk8.bmp
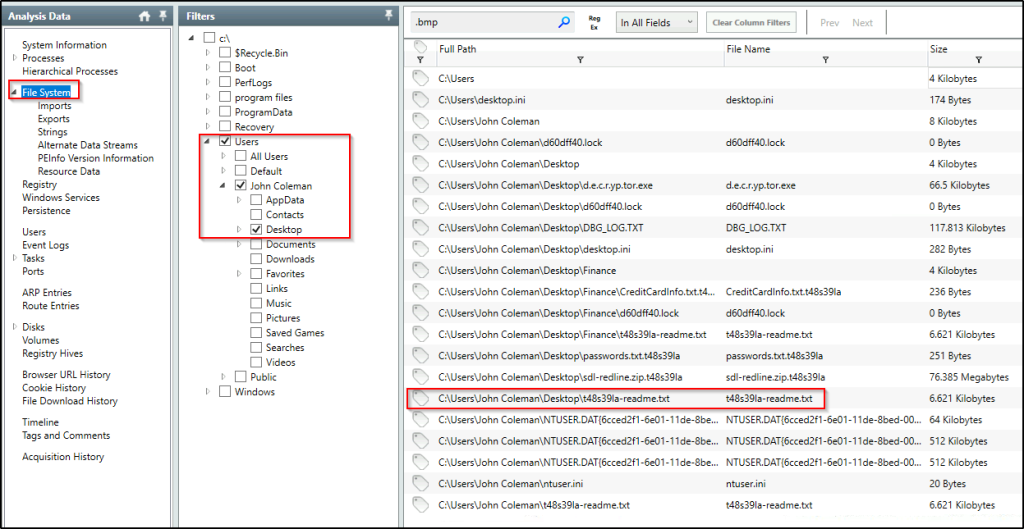
Using the same filter from above, type the extension “.bmp” in the search bar. Filter further in the “Summary” column results that contain the name of the user.
The attacker left a note for the user on the Desktop; provide the name of the note with the extension.
Answer: t48s39la-readme.txt
Go to the user’s Desktop folder and a readme text file can be found in there.
The attacker created a folder “Links for United States” under C:\Users\John Coleman\Favorites\ and left a file there. Provide the name of the file.
Answer: GobiernoUSA.gov.url.t48s39la
Go to the said folder and an very obvious file can be found.
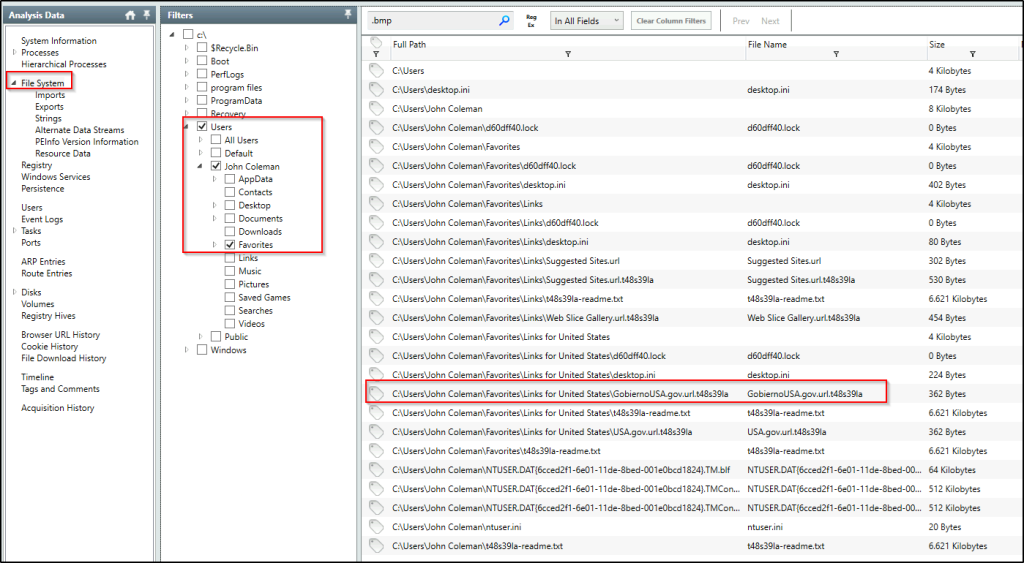
There is a hidden file that was created on the user’s Desktop that has 0 bytes. Provide the name of the hidden file.
Answer: d60dff40.lock
Go to the user’s Desktop folder and we see a file with zero bytes.
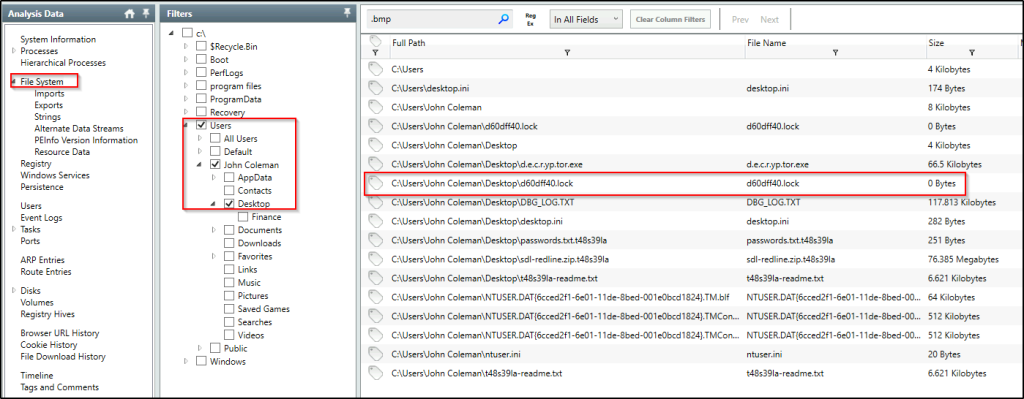
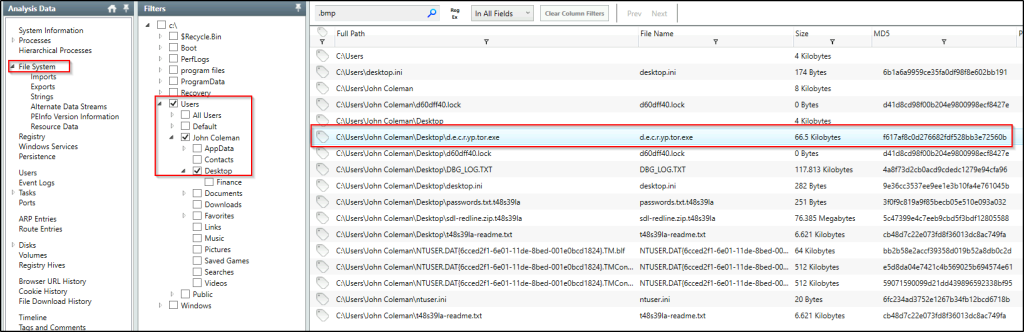
The user downloaded a decryptor hoping to decrypt all the files, but he failed. Provide the MD5 hash of the decryptor file.
Answer: f617af8c0d276682fdf528bb3e72560b
Go to the user’s Desktop folder and another obvious file for decrypting can be found.
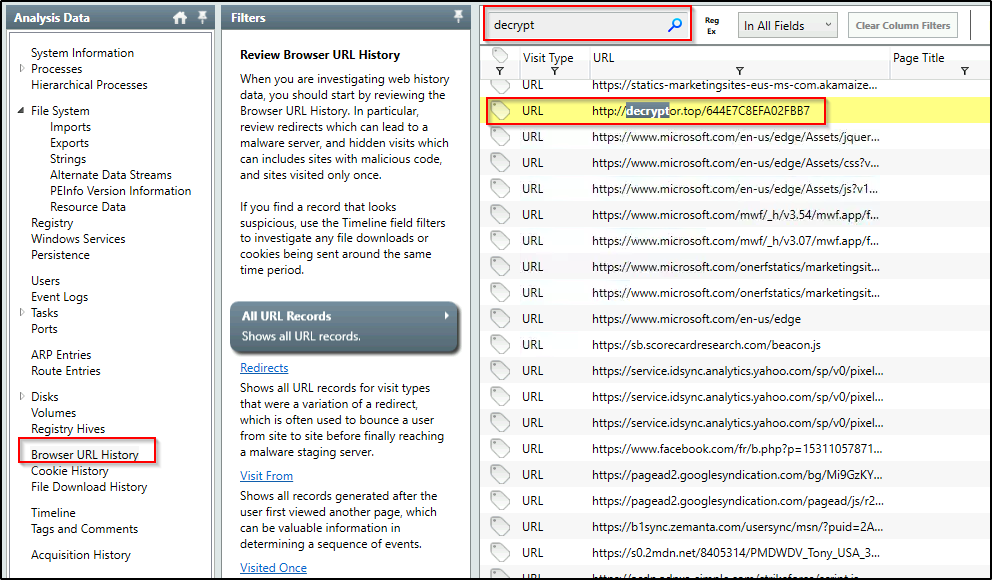
In the ransomware note, the attacker provided a URL that is accessible through the normal browser in order to decrypt one of the encrypted files for free. The user attempted to visit it. Provide the full URL path.
Answer: http://decryptor.top/644E7C8EFA02FBB7
The URL can be found in the “Browser URL History”. Filter results with “decryp” as keyword.
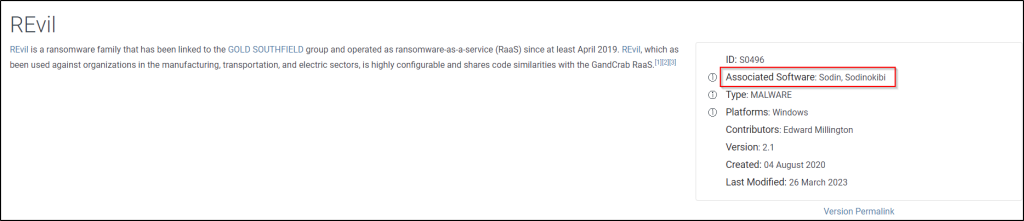
What are some three names associated with the malware which infected this host? (enter the names in alphabetical order)
Answer: REvil, Sodin, Sodinokibi
Search on Mitre ATT@CK framework.
Thank you for reading. Until next time. 🙂


Leave a comment