In this blog, I’ll be documenting my experience with the Disk Analysis & Autopsy room on TryHackMe, which challenged me to leverage disk artifacts to unravel an attack narrative.
Room Link: https://tryhackme.com/room/autopsy2ze0
Task 1 Windows 10 Disk Image
In the attached VM, there is an Autopsy case file and its corresponding disk image. After loading the .aut file, make sure to re-point Autopsy to the disk image file.
Start Autopsy and select “Open Case”

Select the “.aut” file.
Select the image “HASAN2.E01”
Ingest Modules were already ran for your convenience.
Your task is to perform a manual analysis of the artifacts discovered by Autopsy to answer the questions below.
This room should help to reinforce what you learned in the Autopsy room. Have fun investigating!
RDP Machine Details:
- IP:
MACHINE_IP - Username:
administrator - Password:
letmein123!
Answer the questions below
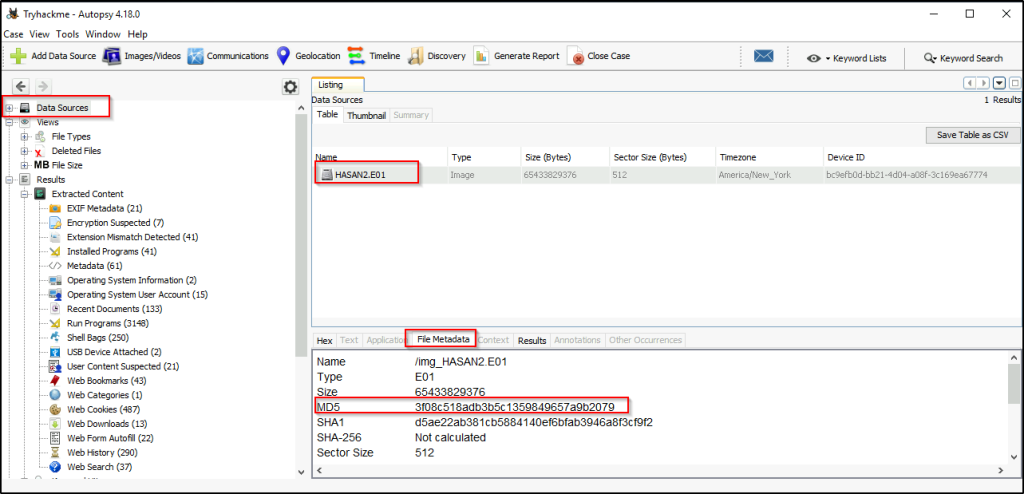
What is the MD5 hash of the E01 image?
Answer: 3f08c518adb3b5c1359849657a9b2079
Click the “Data Source” tree, and on the right panel, there is metadata of the file.
What is the computer account name?
Answer: DESKTOP-0R59DJ3
Expand the “Expanded Content” under the “Results” tree. Click “Operating System Information” and the right panel will display the name of the computer.
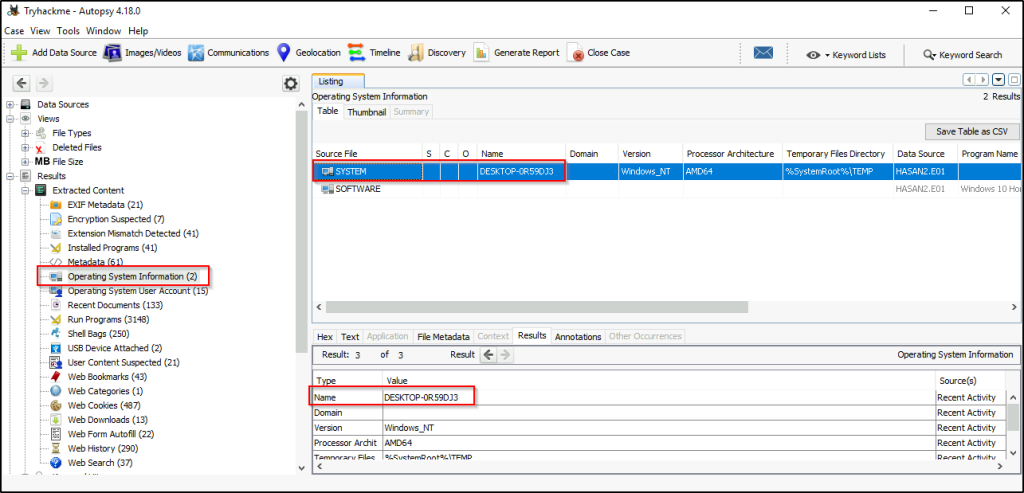
List all the user accounts. (alphabetical order)
Answer: H4S4N,joshwa,keshav,sandhya,shreya, sivapriya,srini,suba
The specific relevant content for this request, if necessary, delimited with characters: Select “Operating System User Account” and sort by “User ID”. Regular users are those starting with UID of 1000.
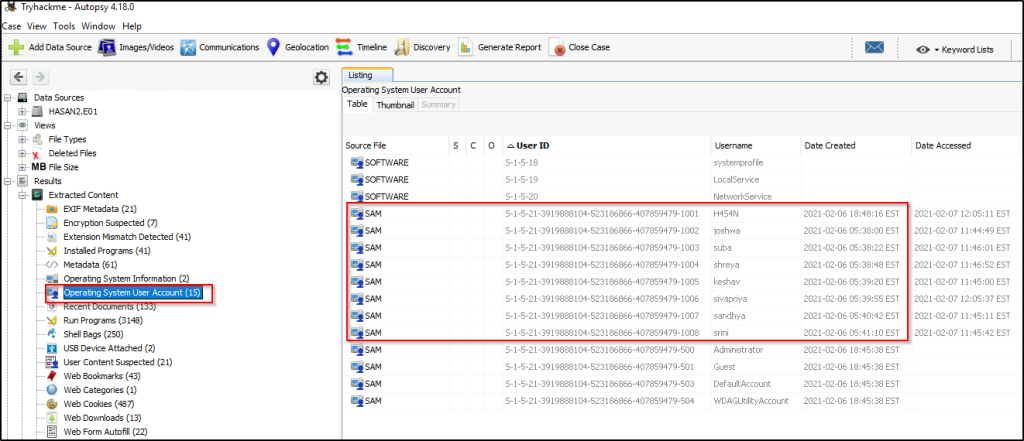
Who was the last user to log into the computer?
Answer: sivapriya
This time around, sort it by “Date Accessed”.
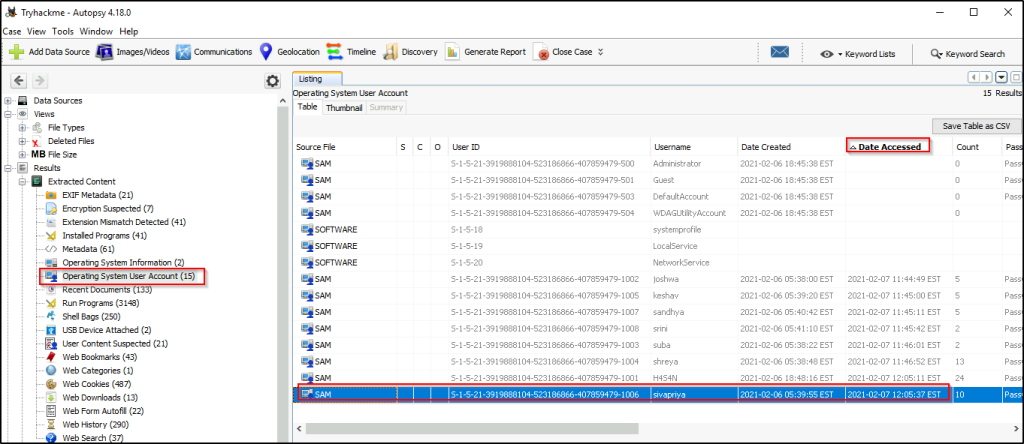
What was the IP address of the computer?
Answer: 192.168.130.216
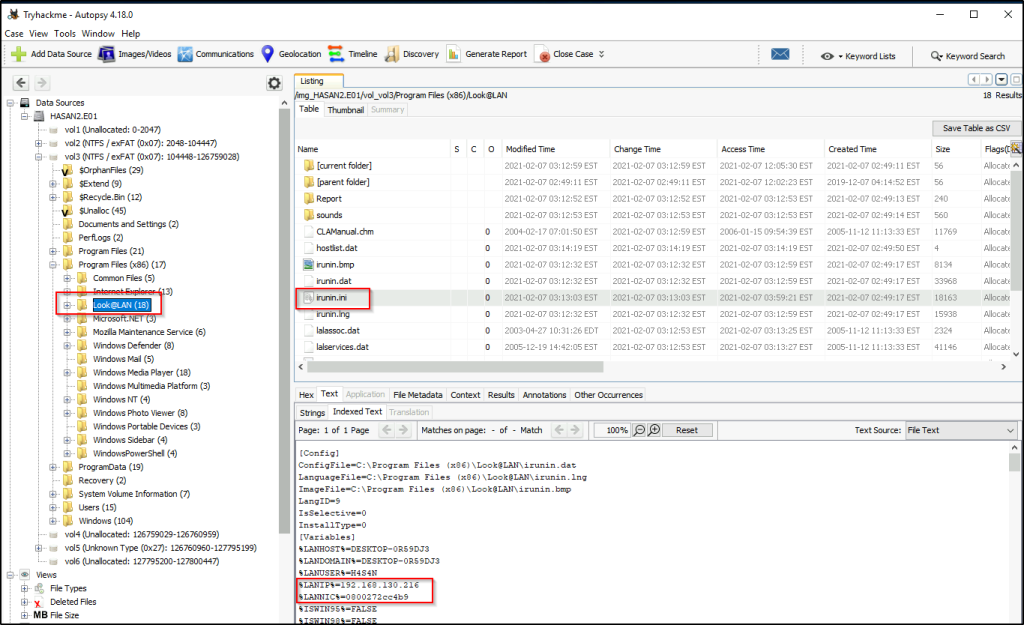
Head on to the location of “Program Files”, and in it is a tool for network monitoring. Expand the folder within the folder is a file that contains the network information of the system. The variable “LANIP” contains the IP value of the system.

What was the MAC address of the computer? (XX-XX-XX-XX-XX-XX)
Answer: 08-00-27-2c-c4-b9
From the same location, the MAC address is found in the variable “LANNIC”. Edit the value in MAC address format.
What is the name of the network card on this computer?
Answer: Intel(R) PRO/1000 MT Desktop Adapter
For network connections, we can search the registry hive “SOFTWARE\Microsoft\Windows NT\CurrentVersion” where the “ROOT” location is “C:\Windows\system32\config”.
We can also double-click on “SOFTWARE” and it will take us to the “ROOT” location.
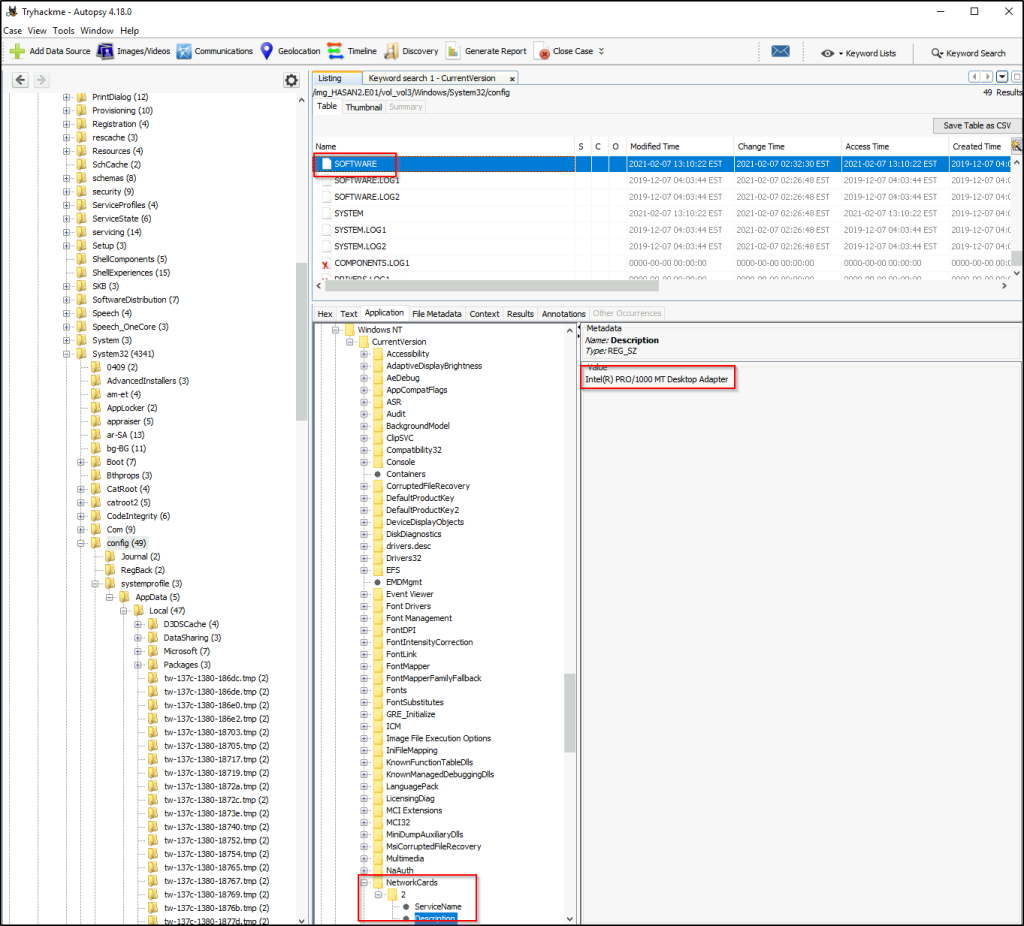
Within “CurrentVersion” is a key called “NetworkCards” and within it is a subkey called “2”. And we can see the name of the adapter in the “Description” key value.
What is the name of the network monitoring tool?
Answer: Look@LAN
As observed from above, a tool was used to monitor network traffic. Another way to search for it is to look under the “Installed Program” and be critical of software that are suspicious.


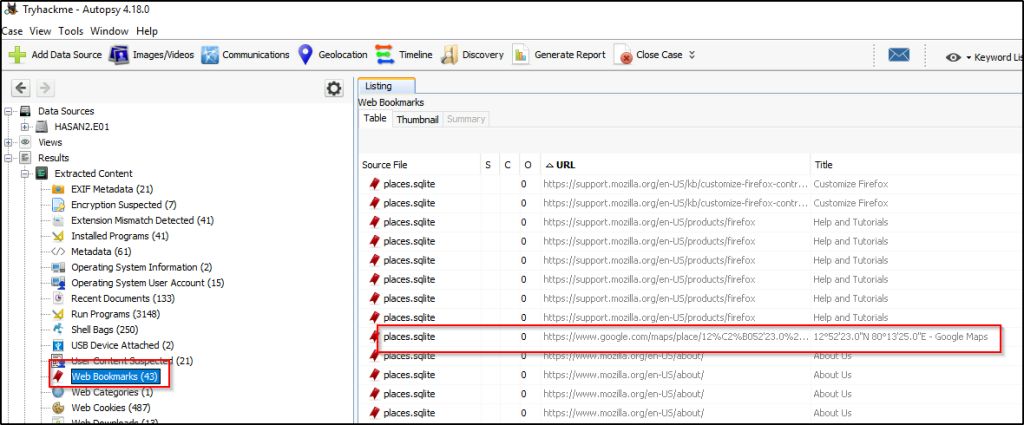
A user bookmarked a Google Maps location. What are the coordinates of the location?
Answer: 12°52’23.0″N 80°13’25.0″E
In the “Extracted Content” is a web bookmark that contains information of bookmarked URLs.
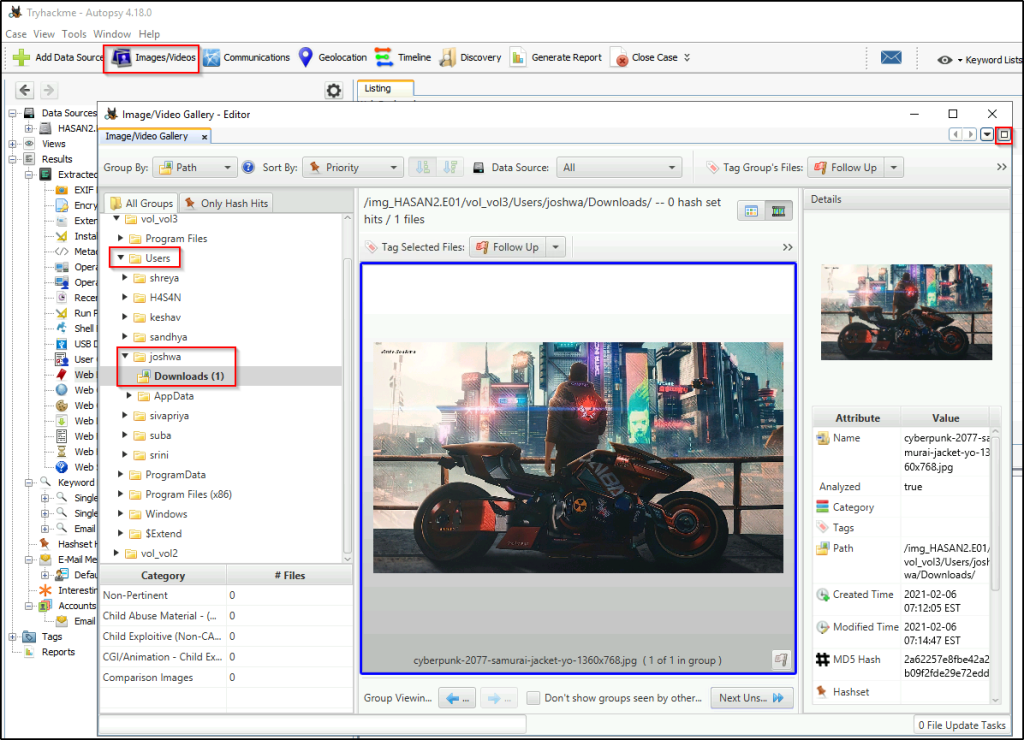
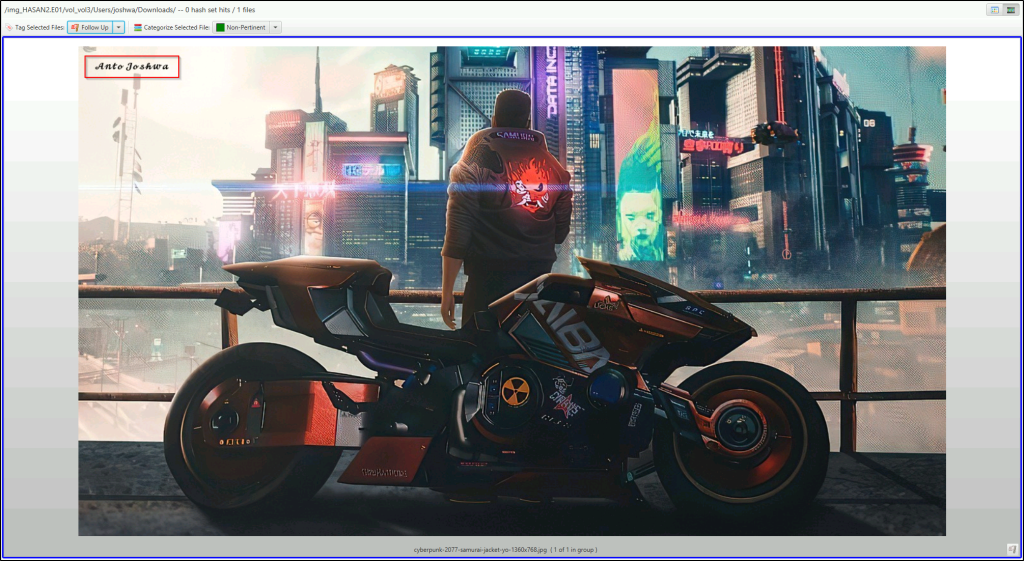
A user has his full name printed on his desktop wallpaper. What is the user’s full name?
Answer: Anto Joshwa
Click on the “Images/Videos” tab to display images or videos that were extracted. Go through all the users’ directories. User “joshua” has an image in the “Downloads” folder. Expand the window, and it can be seen that the user’s full name was printed on the image.
A user had a file on her desktop. It had a flag but she changed the flag using PowerShell. What was the first flag?
Answer: flag{HarleyQuinnForQueen}
Check the PowerShell history for each user. Here, we see in user Shreya’s PowerShell history that the initial flag of ‘I hacked you’ of the text file was changed to ‘flag{HarleyQuinnForQueen}’.

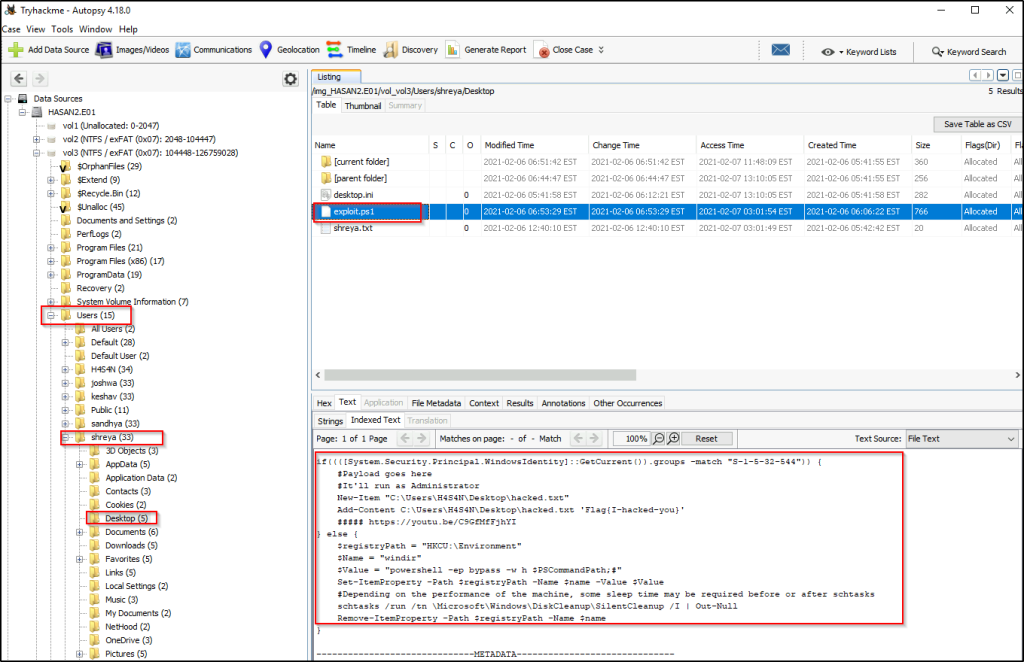
The same user found an exploit to escalate privileges on the computer. What was the message to the device owner?
Answer: Flag{I-hacked-you}
Going to Shreya’s desktop folder, we see a PowerShell script that will elevate privileges on the computer. We can also see a text file that will be created once the script is executed, which will add the content ‘I hacked you’.
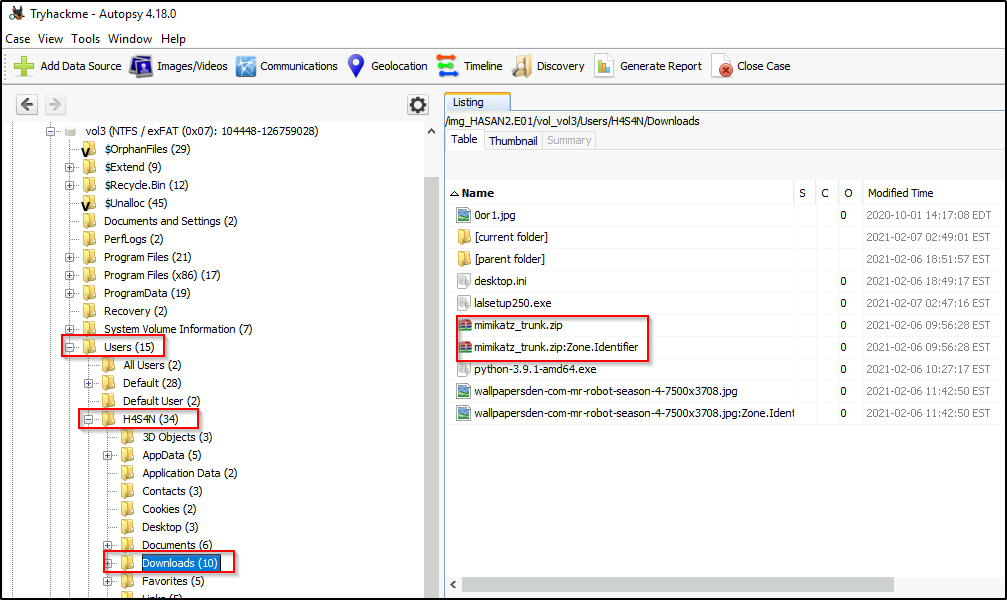
2 hack tools focused on passwords were found in the system. What are the names of these tools? (alphabetical order)
Answer: lazagne,mimikatz
The first tool can be located in a user’s download folder, where a very popular tool used for dumping credentials was probably downloaded.
We can also look at the “prefetch” file to find information about programs that were executed. Here is an unfamiliar tool, but with Googling, I found out that it is also used for retrieving passwords.
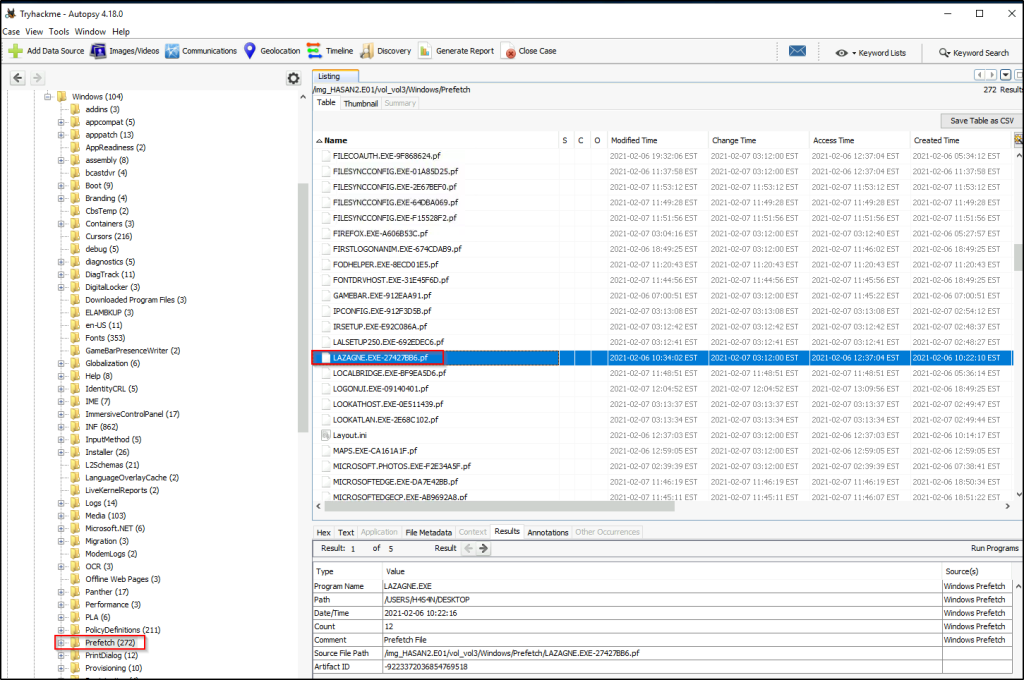
The said program can also be found in the “Run Programs” under the “Results” tree.

There is a YARA file on the computer. Inspect the file. What is the name of the author?
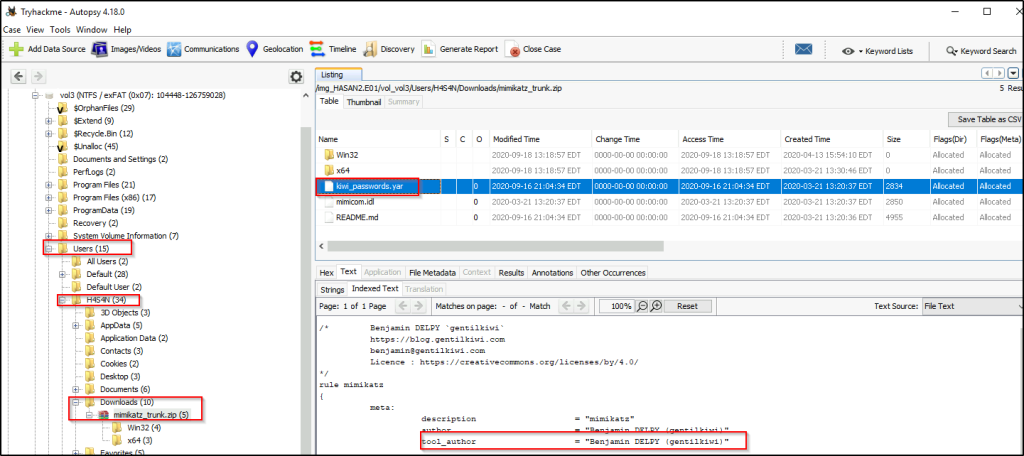
Benjamin DELPY (gentilkiwi)
We can search for files that have a “.yar” extension.

If we click on the file found, we see more info about the file like its location.
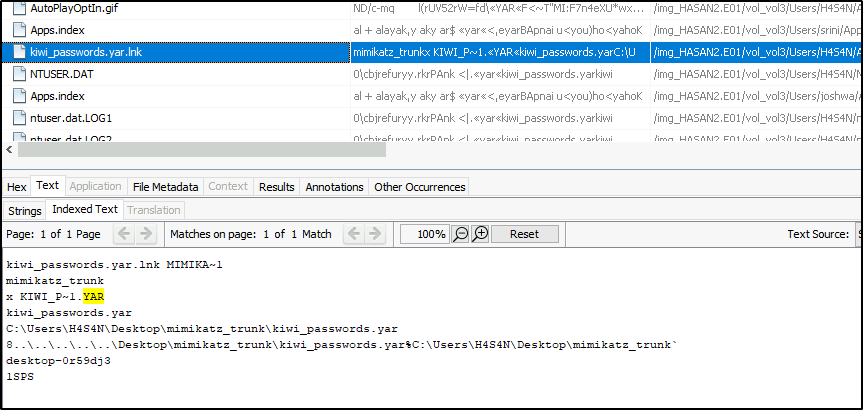
The file cannot be located on the “Desktop” folder, but as identified earlier, there was a “mimikatz” file in the “Downloads” folder of the same user.

Click on the file and the metadata will show the author of mimikatz.
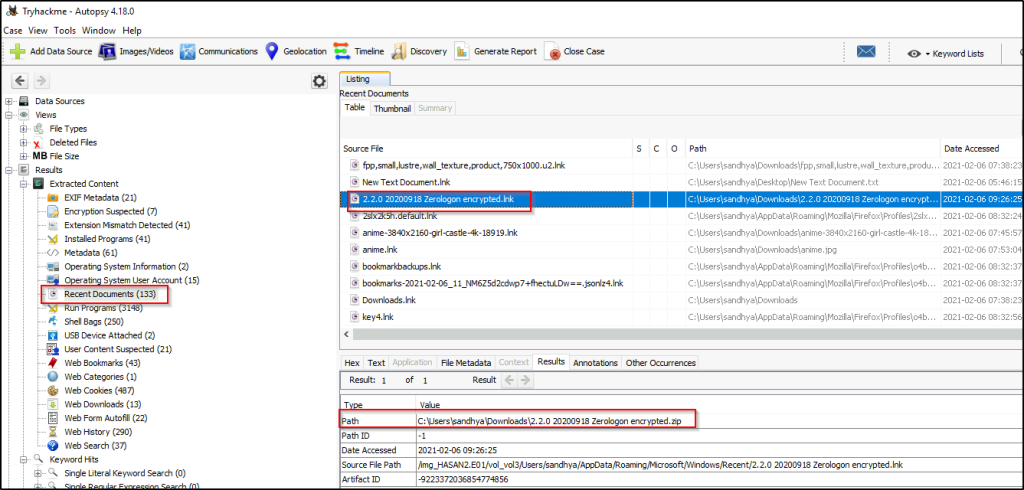
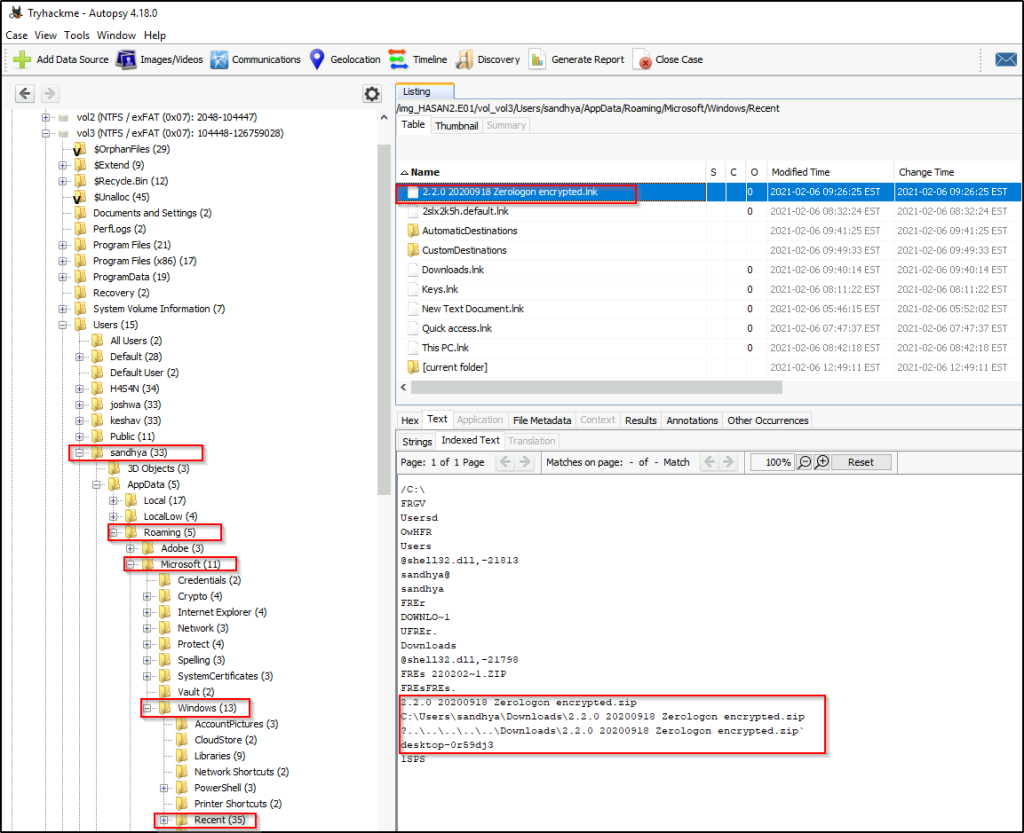
One of the users wanted to exploit a domain controller with an MS-NRPC based exploit. What is the filename of the archive that you found? (include the spaces in your answer)
Answer: 2.2.0 20200918 Zerologon encrypted.zip
Going over the “Recent Documents”, there was an exploit downloaded that will take advantage of “Zerologon”.

Thank you for reading. Until next time. 🙂


Leave a comment